Privileged Access Management Policy Template
Privileged Access Management Policy Template - Access controls manage the admittance of users to system and network resources by granting users access only to the specific resources they require to complete their job. 21 jan 2021 page 1 of 10 privileged access management standard. They are based on compliance requirements outlined by. Web identity and access management policy. Web sans has developed a set of information security policy templates. Privileged access management (pam) plays a key role. They are based on compliance requirements outlined by. The purpose of this policy is to prevent inappropriate granting and use of privileged access by irt staff, application super users, departmental. Access control policies are an. Web privileged user account access policy. Access control policies are an. 01 may 2021 last revised date: Web sans has developed a set of information security policy templates. The purpose of this policy is to ensure that no unauthorized user can access unfpa servers with privileged. How to write an iso 27001 access control policy (with a free template) luke irwin 5th july 2021. Last updated on february 12, 2024. They are based on compliance requirements outlined by. The purpose of this policy is to ensure that no unauthorized user can access unfpa servers with privileged. The principle of least privilege must be. The purpose of this policy is to define required access control measures to all university systems and applications to protect. They are based on compliance requirements outlined by cis, nist, pci and. Web privileged user account access policy. Web privileged access management standard effective date: Improper user access review management. 21 jan 2021 page 1 of 10 privileged access management standard. This article guides you through enabling and configuring privileged. Web a privileged account is required when accessing resources that are managed by msu it and when a user must assume levels of privilege that may allow the user to expose. Web how to perform user access reviews: Last updated on february 12, 2024. Privileged access management (pam) plays a key. Privileged access management (pam) plays a key role. Access control policies are an. The principle of least privilege must be. Web privileged user account access policy. They are based on compliance requirements outlined by cis, nist, pci and. Access control policies are an. The purpose of this policy is to prevent inappropriate granting and use of privileged access by irt staff, application super users, departmental. Web where technically feasible privileged access users must use the university approved privileged access management system. 01 may 2021 last revised date: The purpose of this policy is to ensure that no unauthorized. 01 may 2021 last revised date: It’s essential to prioritize as a cyber defense mechanism. They are based on compliance requirements outlined by. Improper user access review management. They are based on compliance requirements outlined by cis, nist, pci and. Web privileged access management standard effective date: How to write an iso 27001 access control policy (with a free template) luke irwin 5th july 2021. Web privileged access management (pam) helps organizations manage their privileged accounts in order to protect their critical assets, meet compliance regulations and to. The principle of least privilege must be. Web sans has developed a. Improper user access review management. This article guides you through enabling and configuring privileged. Privileged access management (pam) plays a key role. They are based on compliance requirements outlined by. 01 may 2021 last revised date: The principle of least privilege must be. This article guides you through enabling and configuring privileged. Web how to perform user access reviews: Web sans has developed a set of information security policy templates. Web privileged access management standard effective date: Access controls manage the admittance of users to system and network resources by granting users access only to the specific resources they require to complete their job. How to write an iso 27001 access control policy (with a free template) luke irwin 5th july 2021. It’s essential to prioritize as a cyber defense mechanism. Web pam audit checklist: 01 may 2021 last revised date: Improper user access review management. Privileged access management (pam) plays a key role. The purpose of this policy is to ensure that no unauthorized user can access unfpa servers with privileged. Web identity and access management policy. Web a privileged account is required when accessing resources that are managed by msu it and when a user must assume levels of privilege that may allow the user to expose. Web privileged access management standard effective date: They are based on compliance requirements outlined by. They are based on compliance requirements outlined by cis, nist, pci and. Web where technically feasible privileged access users must use the university approved privileged access management system. They are based on compliance. The principle of least privilege must be.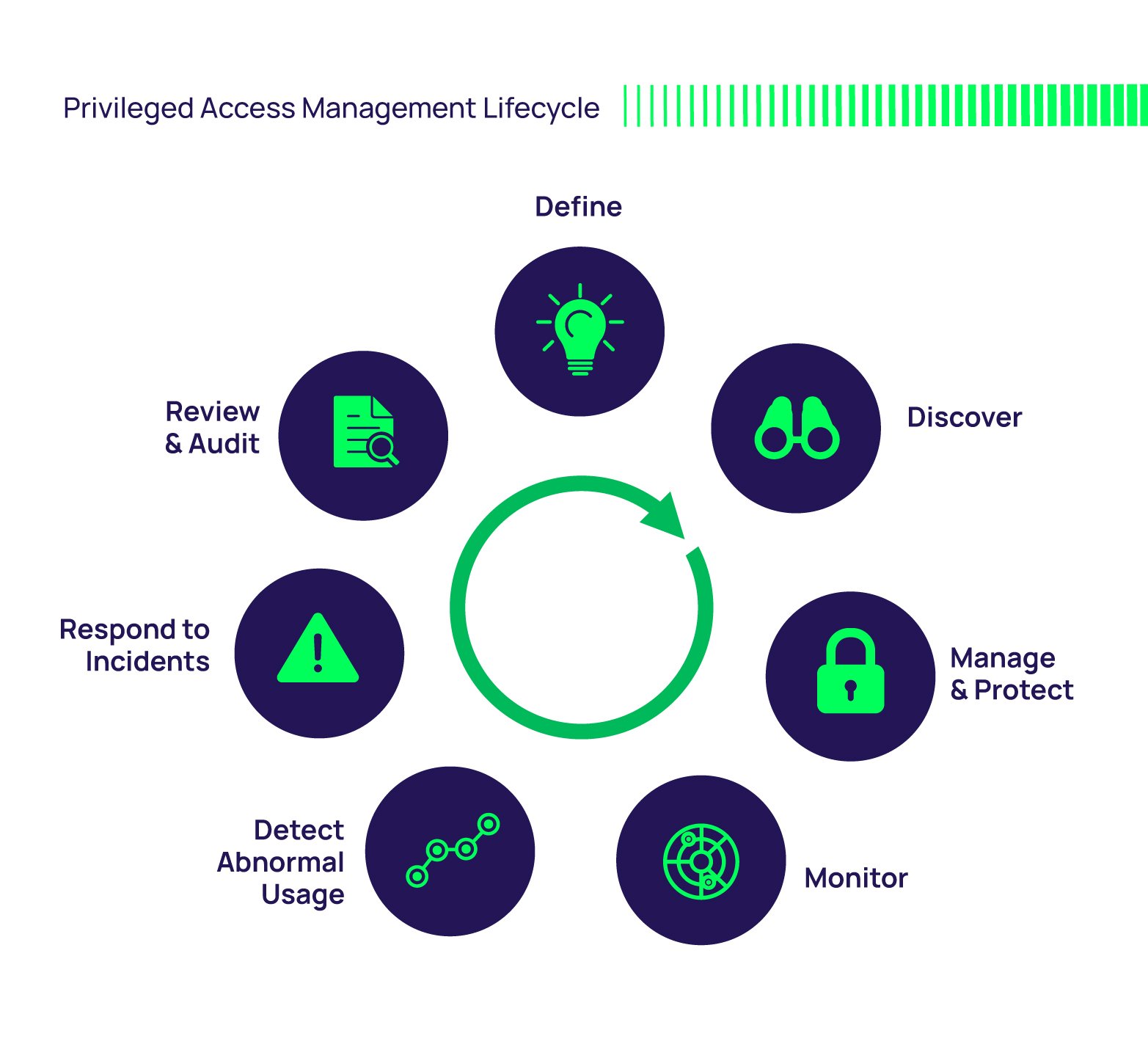
What is Privileged Access Management (PAM)? Delinea

What is Privileged Access Management (PAM)? (2023)
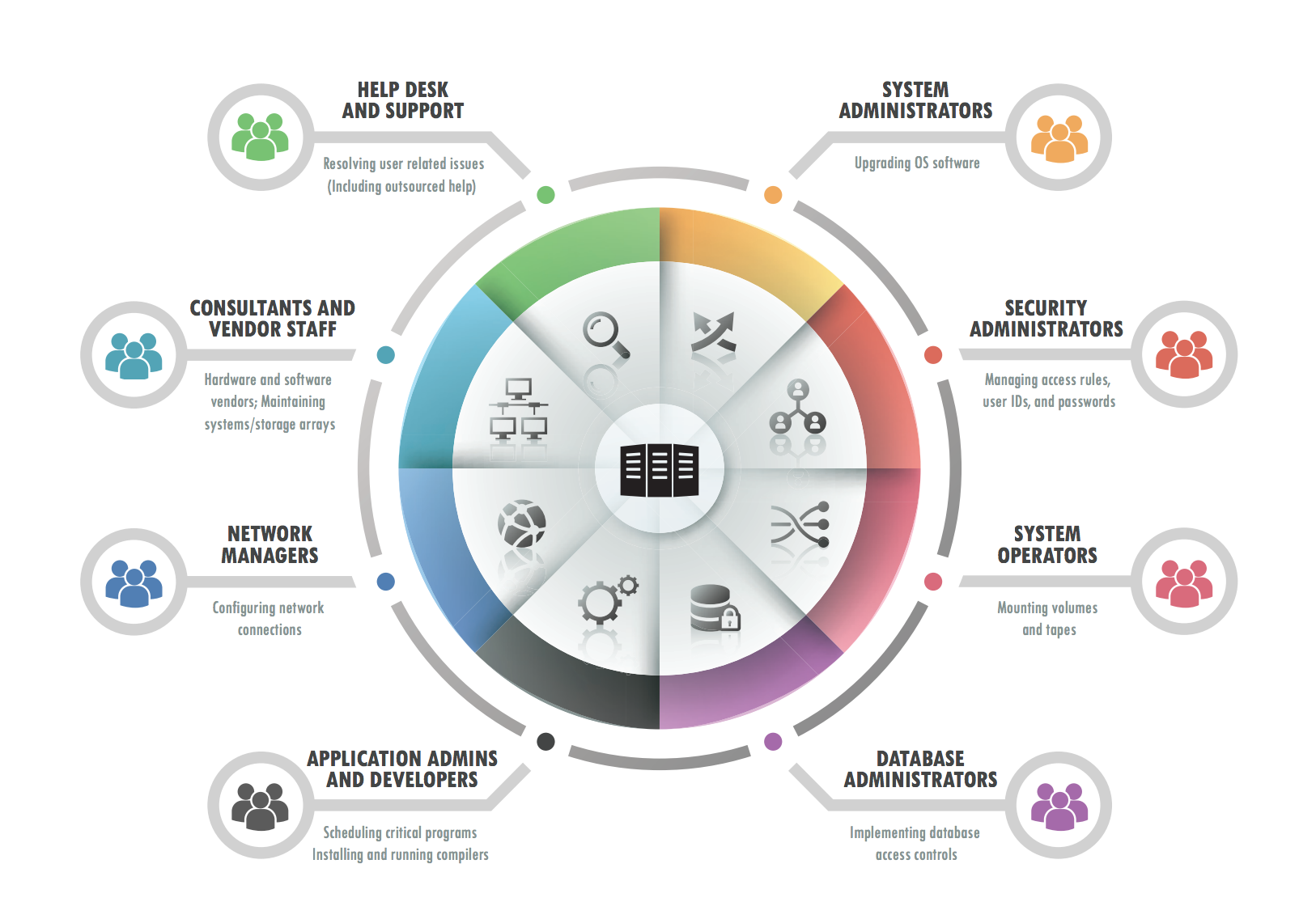
Essentials of Privileged Access Management Fortra
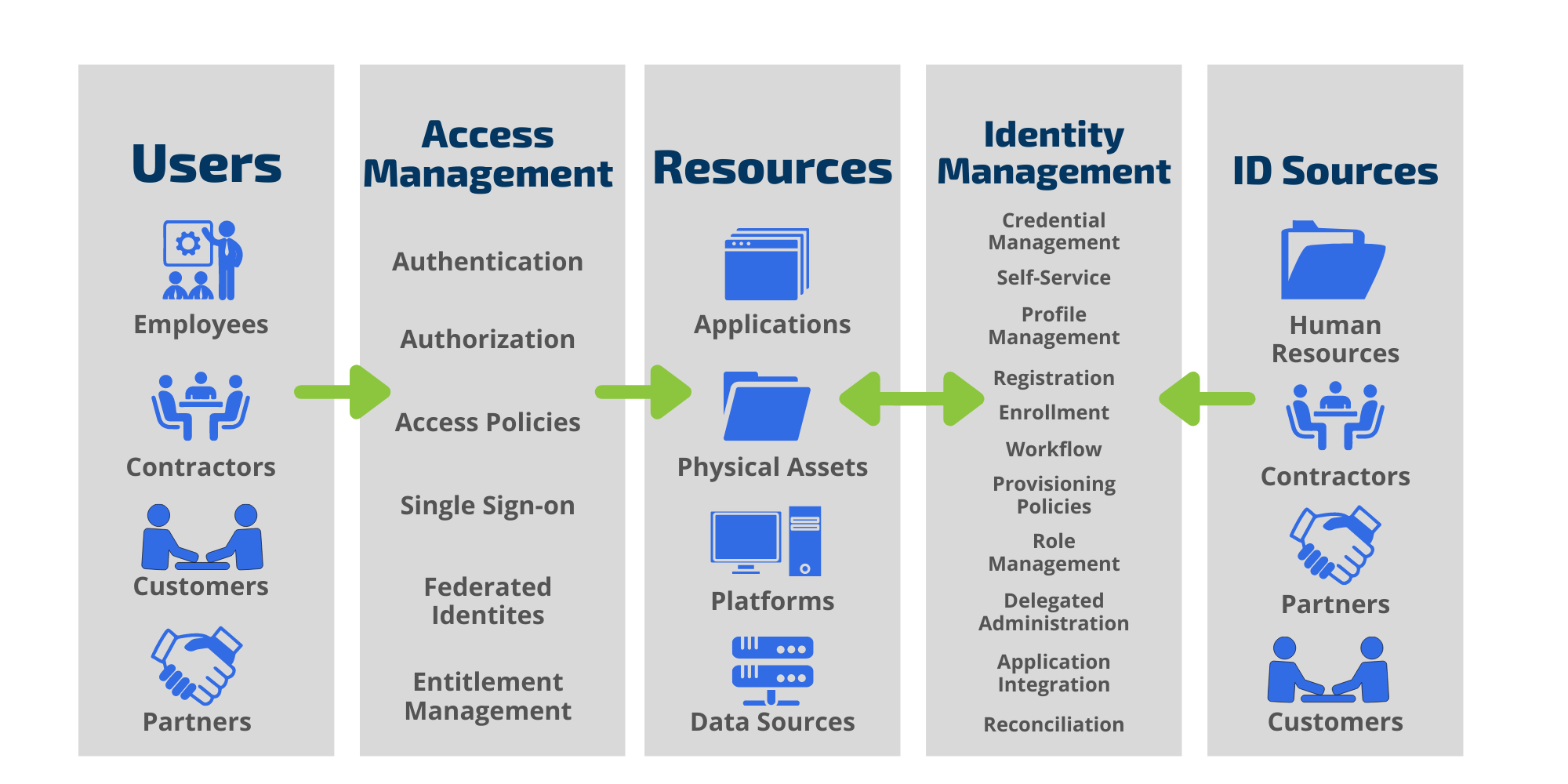
Understanding Key Identity & Access Management Components Blog

Key Management Policy Template

Privileged Access Management Policy Template

Download Privileged Access Management Policy Template Whitepaper

What is Privileged Access Management? Why It Should Be a Security Priority

Advantages of Privileged Access Management Services for Compliance with
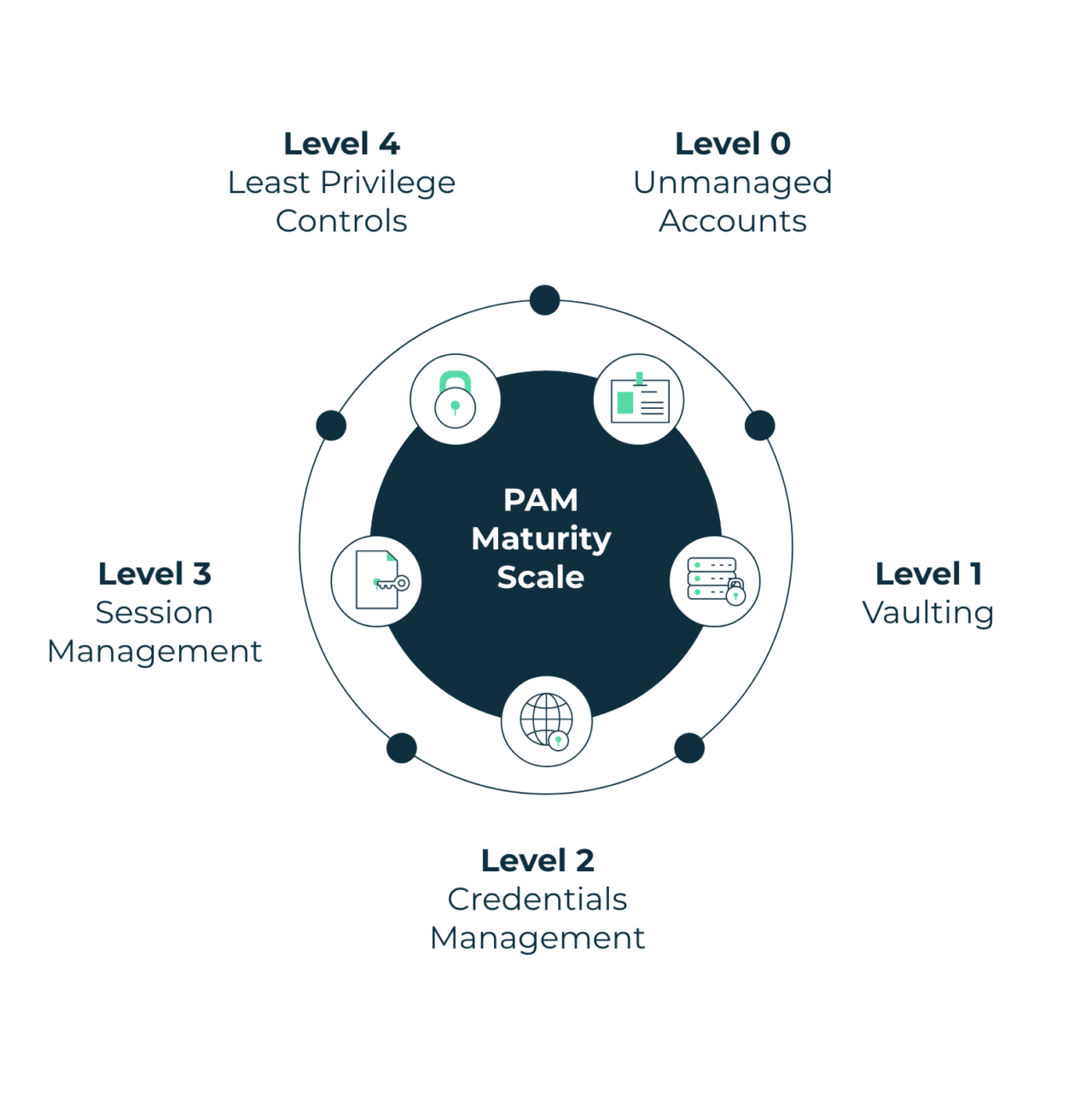
Privileged Access Management (PAM) SecureISS
Web One Of The First Steps To Privileged Access Management (Pam) Success Is Defining Clear And Consistent Policies That Everyone Who Uses And Manages Privileged Accounts.
21 Jan 2021 Page 1 Of 10 Privileged Access Management Standard.
The Purpose Of This Policy Is To Prevent Inappropriate Granting And Use Of Privileged Access By Irt Staff, Application Super Users, Departmental.
These Are Free To Use And Fully Customizable To Your Company's It Security Practices.
Related Post: